Overview
Requests from any cloud API gateway to your API are passed through the untrusted internet. It means, you have to expose your API on a public IP address but accept requests only from trusted origins. In order to use Nadles, your API needs to make sure that it only accepts requests coming from Nadles API Gateway.Authenticate Nadles API Gateway by API key
You can configure Nadles API Gateway to send an API key to your API with each request. If you’re already using another API gateway, please refer to its documentation on how to set up API key authentication. After you’ve set up your API gateway and issued a new API key for Nadles, continue to the next section to find out how to configure Nadles to send the API key with each request.Configuring Nadles API Gateway
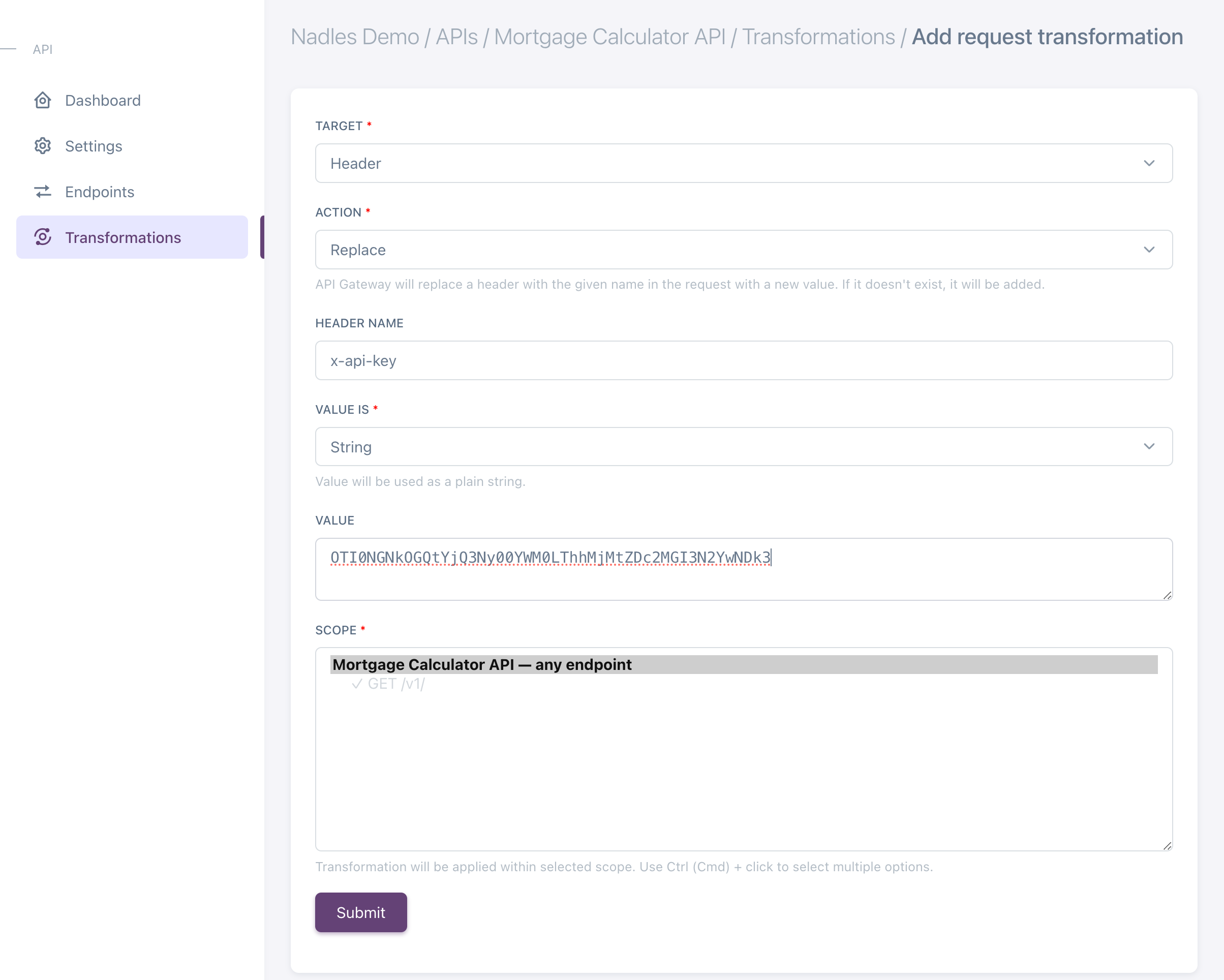
To make Nadles send the API key to your API in a header, you can use the request/response transformation feature. It allows you to add/replace/delete HTTP headers for each proxied request. To make Nadles send the API key with each request:- Navigate to APIs → choose an API → Transformations.
- Click Add new request transformation.
-
Choose Target:
Header, Action:Replace. This will add a header with the given name and value, or replace it with the specified value, if the request already has a header with this name. -
Enter the name of the header in which Nadles API Gateway should send the API key. In the Nginx example above it’s
X-Api-Key. -
Enter the API key in the
Valuefield. Please check the screenshot below for an example. - Click Submit.
X-Api-Key: <value> to each request.
Nginx
If you’re using Nginx as a web server, the easiest way to authenticate Nadles by API keys is to use amap statement together with an if condition as shown below.
X-Api-Key header absent or having a different value than key1.
Replace the key1 with the API key you generated for Nadles API Gateway and reload Nginx.